Publication date of the original Japanese article: 2021-11-02 11:29 (JST)
Translated by. Ryuki Ishii
A variant of the Chaos ransomware targeting Japanese Minecraft users has been reported by cybersecurity firm Fortinet (via PC Gamer). The malware disguises itself as a list of “alt (alternative) accounts” and demands 2,000 yen (approx. $17) to fix the files.
The ransomware is reportedly being distributed through online Minecraft forums under the guise of a list of alt accounts, which are used by players for various purposes, including cheating and trolling. Like most online games, Minecraft’s multiplayer servers are not immune to such behaviors. Cheat tools are used to gain an unfair advantage in PvP servers, and players harass others using the in-game chat and other means.
Last year, Mojang gave moderators the ability to perma-ban players for breaking the game’s community guidelines (official website). Alt accounts are used to avoid getting one’s main account banned, while continuing to engage in malicious activities.
According to Fortinet, the malware file is an executable, “but it uses a text icon to fool potential victims into thinking it is a text file full of compromised usernames and passwords for Minecraft.” Once the damage is done, a ReadMe.txt file demands the victim to pay a ransom. The text is in Japanese only, suggesting that it is indeed targeting Japanese Minecraft players.
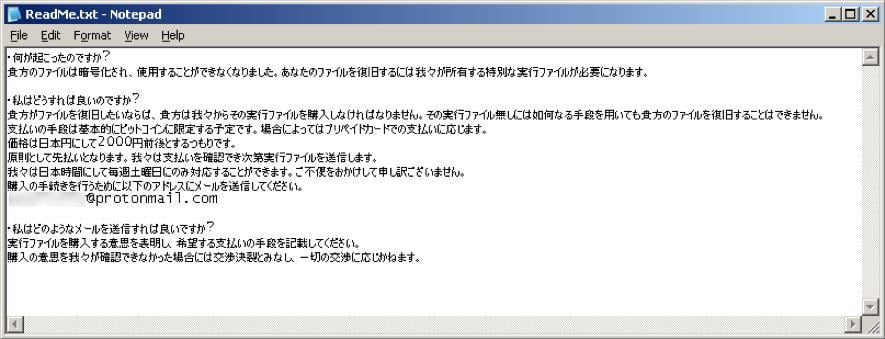
What is interesting about this ransomware is its behavior and ransom amount. When the ransomware is executed, it encrypts all files in the compromised PC that are smaller than about 2.1MB (2,117,152 bytes to be exact) and holds them hostage. On the other hand, Files larger than 2.1MB with specific file extensions “are filled with random bytes so the victim will not be able to get those files back even if the ransom is paid.”
The ransom amount demanded is 2000 yen (approx. $17). This is a very low amount for ransomware. The culprit accepts payment in bitcoin, and in some cases, prepaid cards. There is also a rather polite apology in Japanese stating, “We can only respond on Saturdays (JST). We apologize for any inconvenience caused.”
Fortinet concludes that “despite its cheap ransom demand, its ability to destroy data and render it unrecoverable makes it more than a mere prank to annoy Japanese Minecraft gamers.”
I think it’s also possible that this malware is mainly aimed at young Japanese kids, considering the low ransom, and the fact that prepaid cards can be easily purchased at convenience stores, which Japan has an abundance of.
Buying and selling Minecraft accounts goes against the game’s Terms of Service. And since potential victims are likely trying to get a hold of alt accounts for malign reasons, you could say it’s their own fault if they get scammed. However, the creation and distribution of ransomware is illegal in Japan, and is generally considered an unacceptable act worldwide.
Like Fortinet says, “The best advice is for players to stay off suspicious gaming cheat sites and simply enjoy the game the way it was meant to be played.”
[UPDATE 2021/11/02 17:18 JST]
Amended the article headline to avoid misinterpretation.





